NeverLAN CTF 2020

NeverLAN CTF is a beginner friendly CTF . Me any my friend D4mianWayne did this together, it’s really fun and we enjoyed it. In this post I write a walkthrough for the CTF.
Web
Cookie Monster
 The Webpage:
The Webpage:
The title of the challenge is Cookie Monster
- Google search “cookie monster favorite guy red”
- It’s a character named Elmo
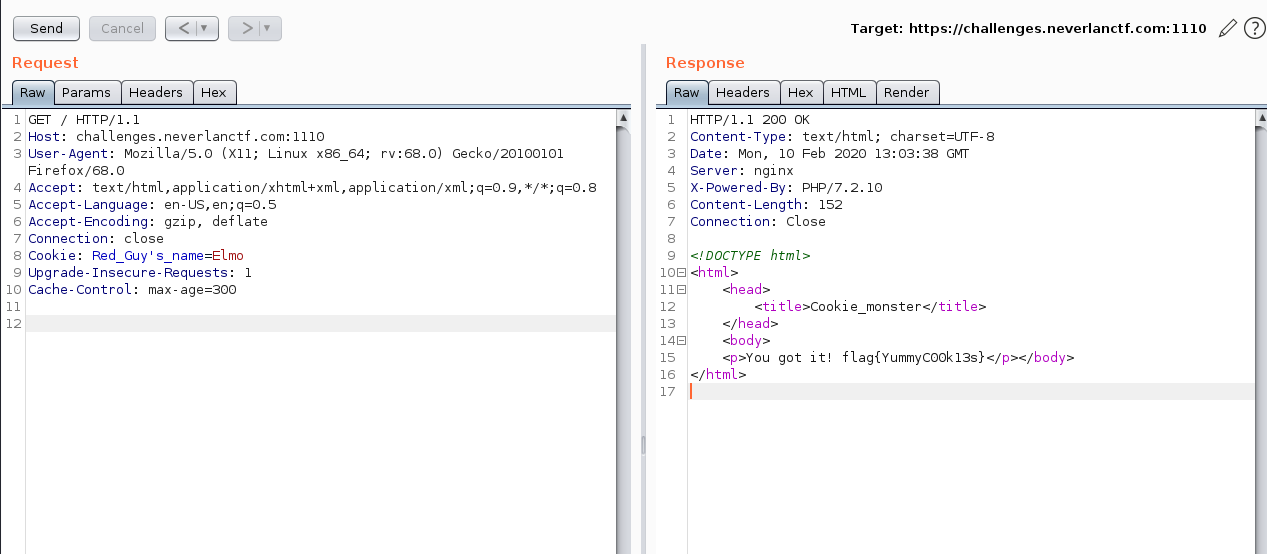
Got the Flag!
Stop the Bot
The Webpage:
It says bot everywhere so I looked at robots.txt
The robots exclusion standard, also known as the robots exclusion protocol or simply robots.txt, is a standard used by websites to communicate with web crawlers and other web robots. The standard specifies how to inform the web robot about which areas of the website should not be processed or scanned.
It shows the files or directories in the webpage.
It shows flag.txt
SQL Breaker
The Webpage:
Found a Login page
Since it is an SQL Breaker I tried some normal sql injection
Source : https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/SQL%20Injection
admin'-- - : admin
It Worked!!
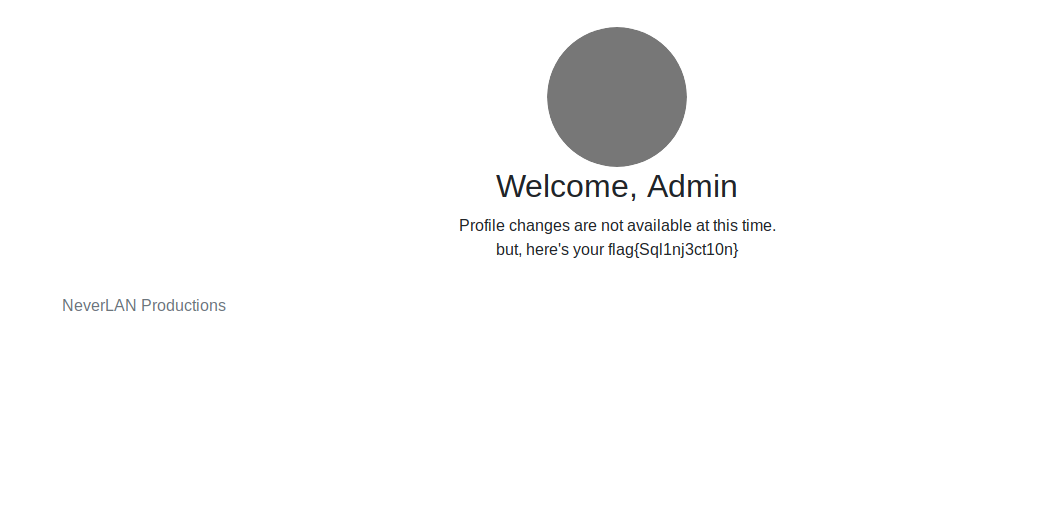
SQL Breaker 2
The Webpage:
Another login page
Like Before I tried some normal SQLi
' or 1=1 limit 1 -- -+
It says only admin user can see the flag, Since the normal sqli works, So adding an offset to the payload (offset 1) will make me select the next from the list.Implicit offset is 0. The 1 in the limit states, show me 1 line of output so if you do LIMIT 1 OFFSET 1. It will give you one line, specifically the second line in the output
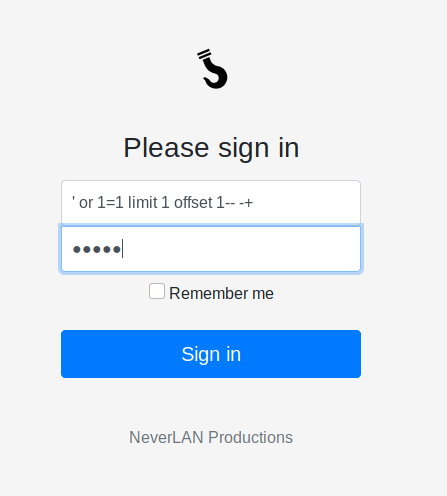
' or 1=1 limit 1 offset 1-- -+
Follow Me!
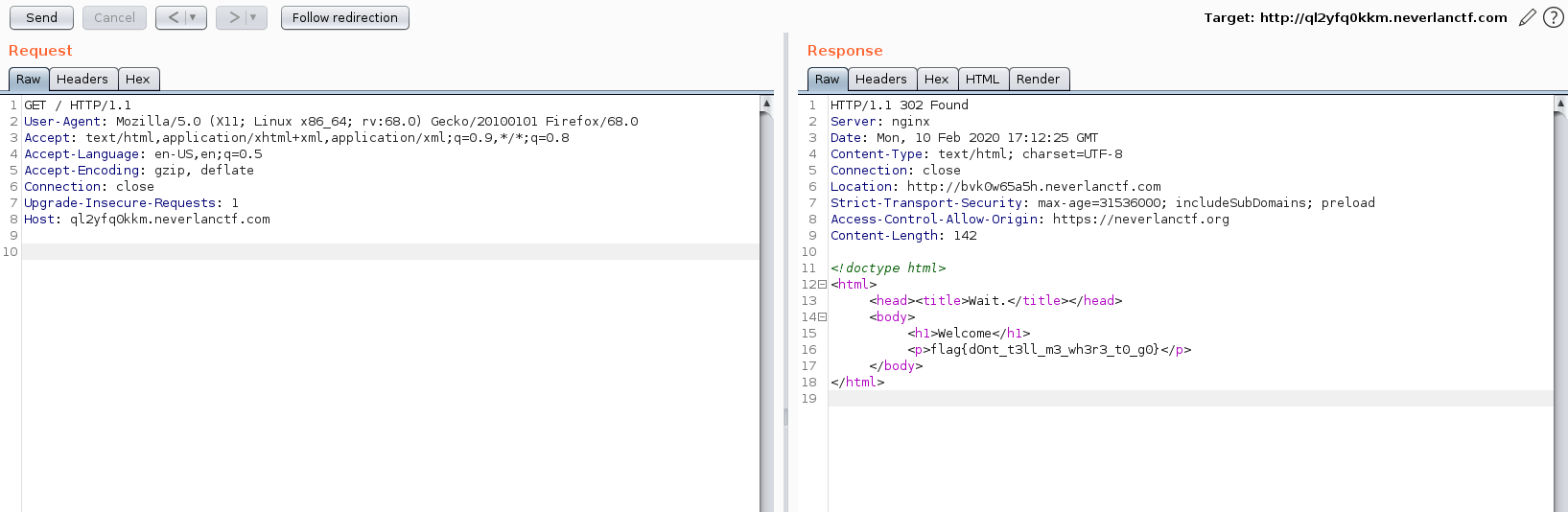
It looks like the page keeps on redirecting ,If a website returns 302 redirect page, browser don’t bother loading the page. So normally we won’t see that data. If we prevent following of redirects, we’ll be able to view the page.
I captured the request in burp and started Follow Redirecion, at a particular domain I got Flag.
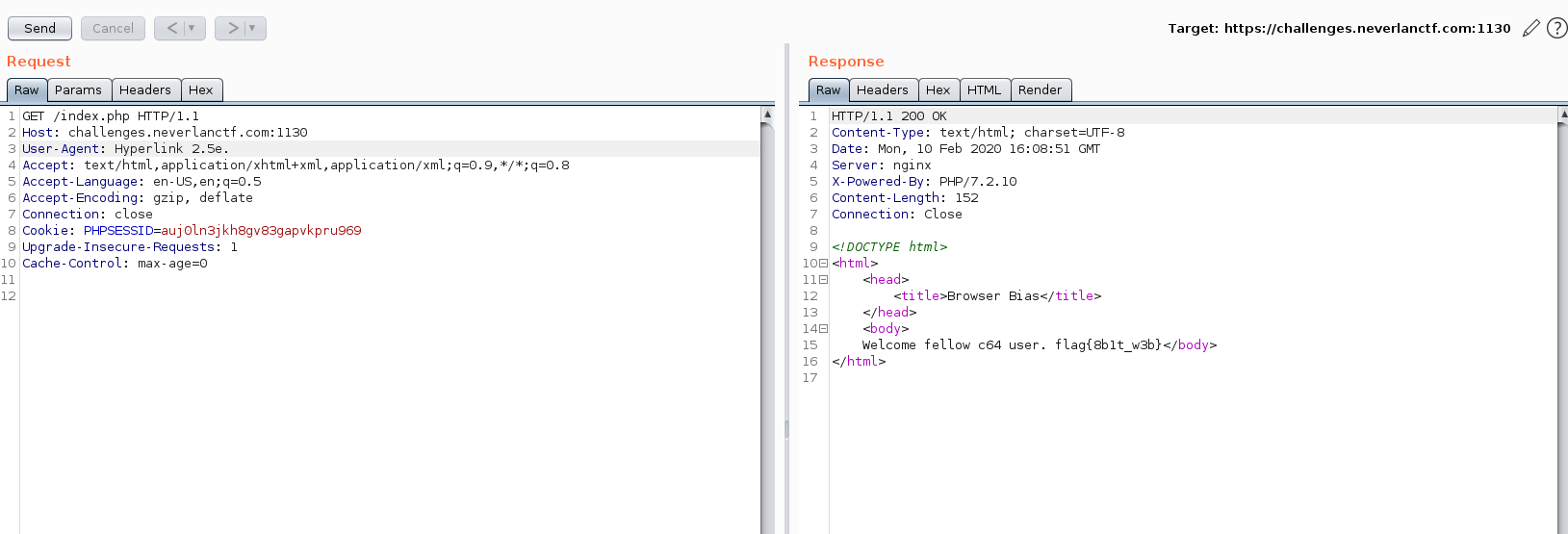
Browser Bias
The Webpage shows us a message that the site is only optimized for browsers that run on commodo 64. So I googled which browser do that.
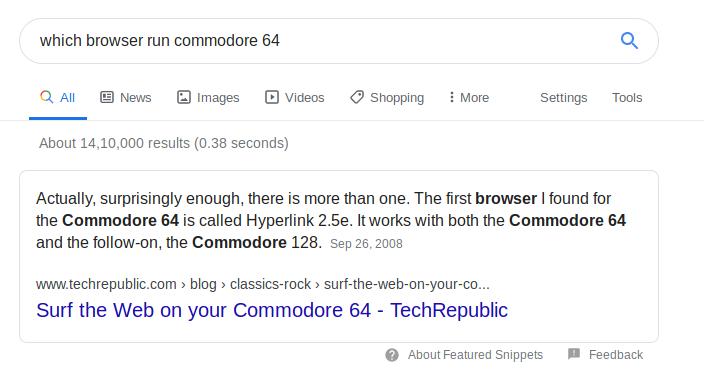
Its Hyperlink 2.5e
So I capture the request in burp and changed the User Agent to Hyperlink 2.5e from Firefox.
PCAP
Unsecured Login
HTTP requires data to be transferred from one point to another over the network. The transfer of resources happens using TCP
So I searched directly as tcp contains flag
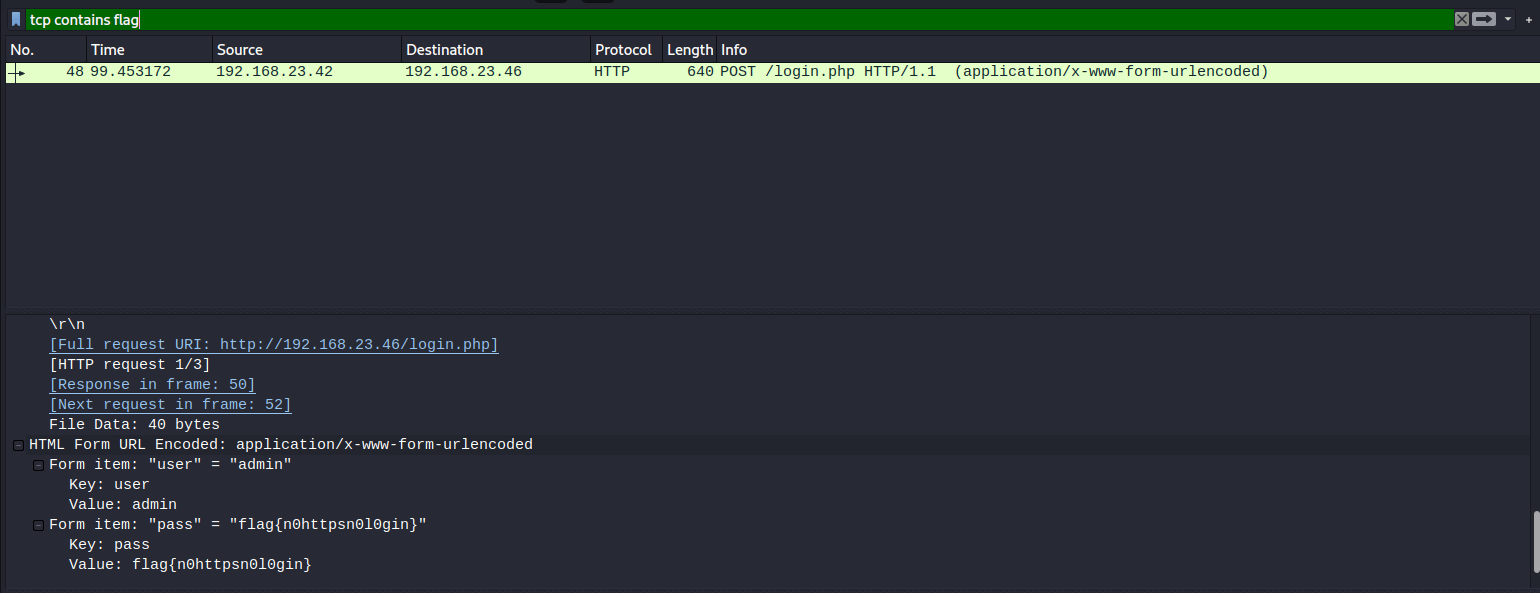
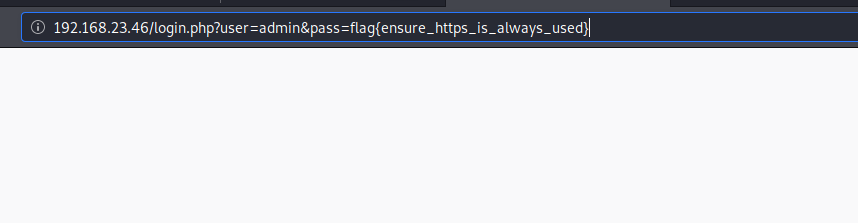
Unsecured Login2
Did the same thing as I did on the first challenge
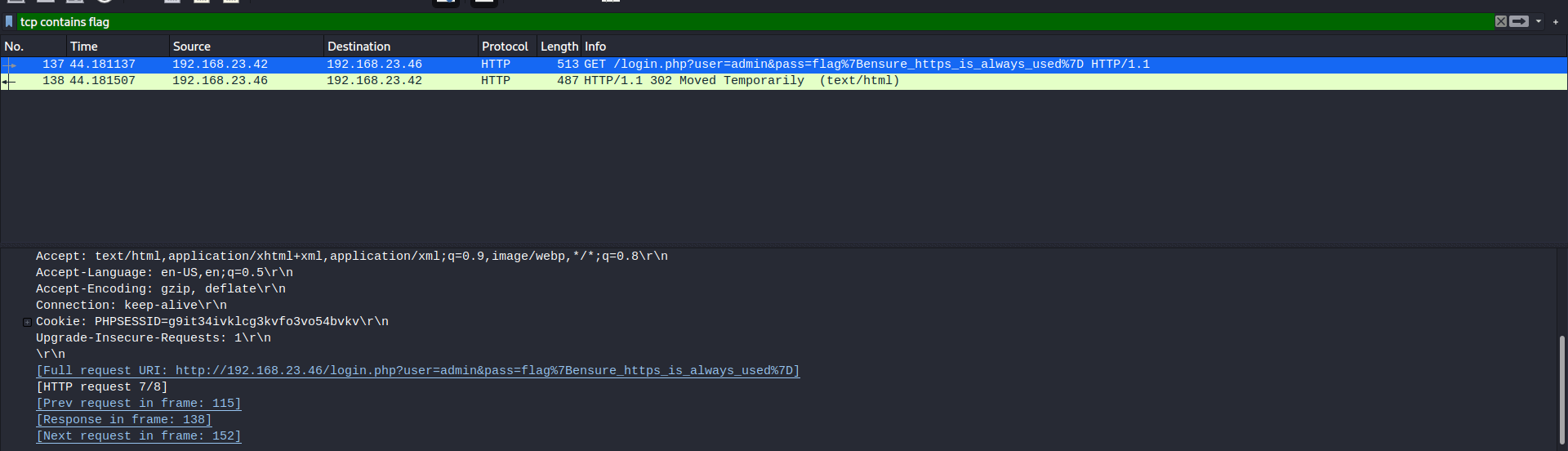
This time flag is in url so I opened it to get the flag
FTP
Since its FTP, I tried searching as FTP and checked each packet in ftp.
Found the flag in FTP-DATA Protocol.
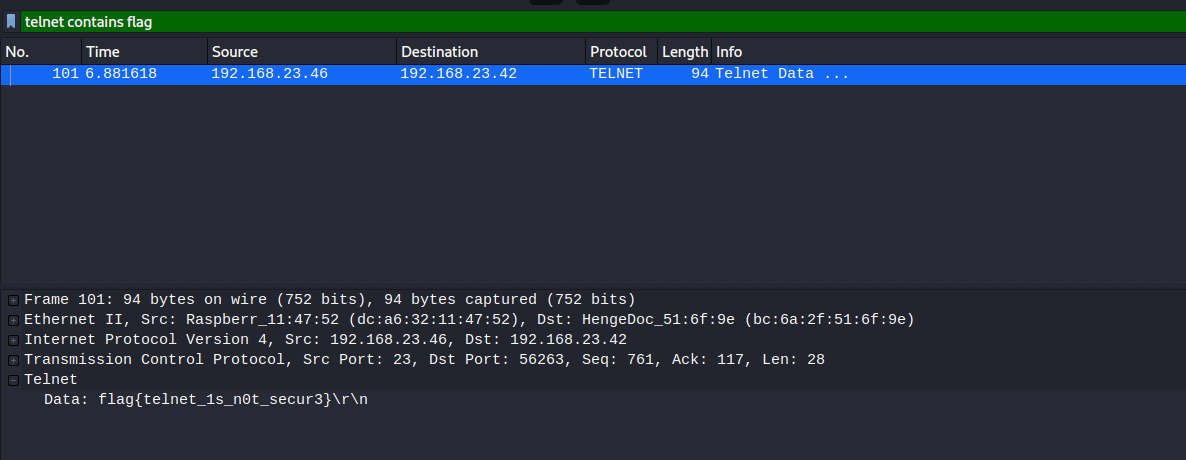
Teletype Network
The file name give me the hint so I searched for telnet contains flag
Hidden ctf on my network
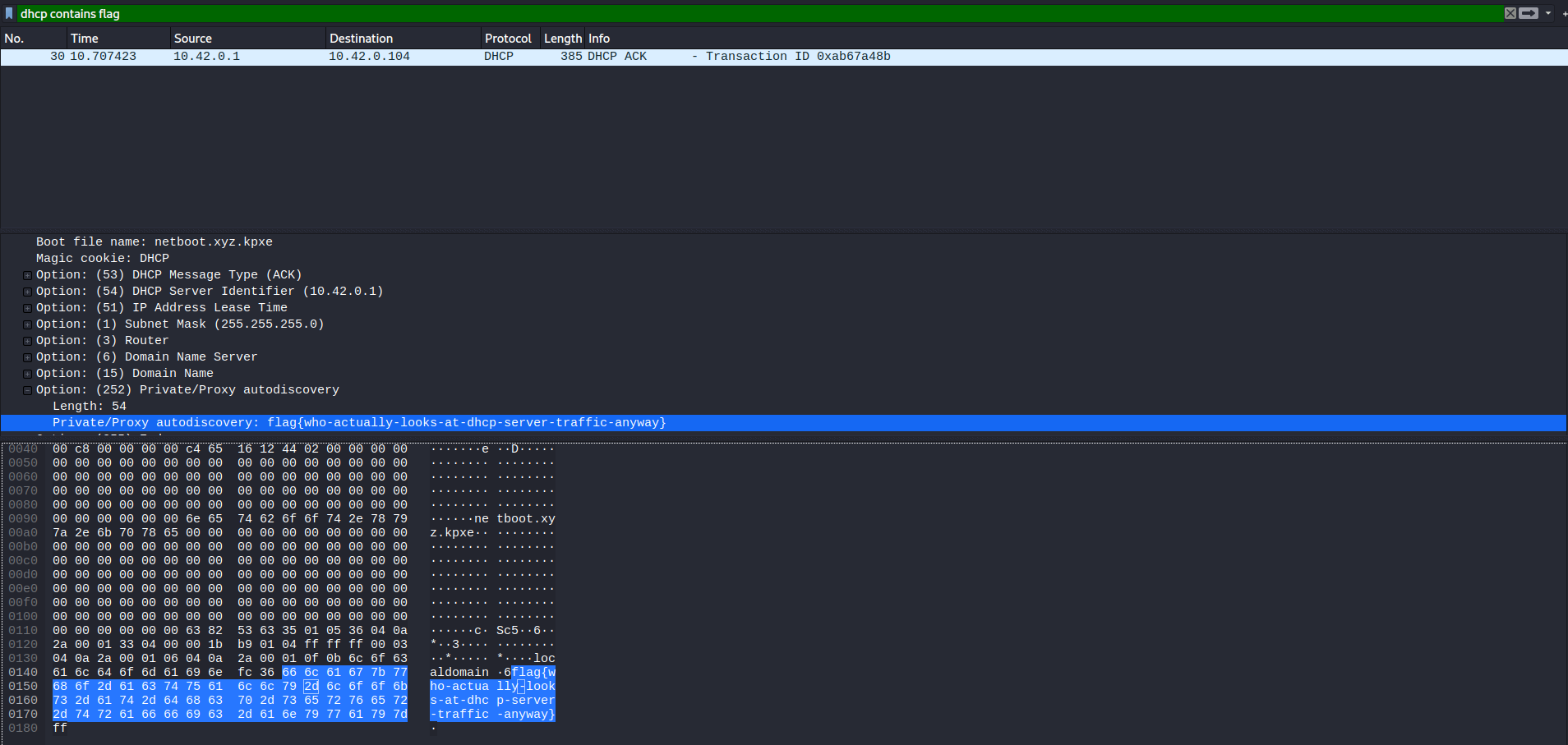
So from the given hint : When a new machine connect to an network , DHCP first assign IP for the machine.
Note
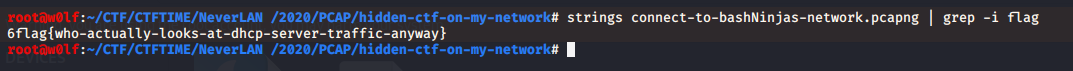
We can even use strings to get flag , because everything in plain text, thats why it works.
RECON
Front Page of the Internet
I googled Front Page of the Internet and found it is reddit
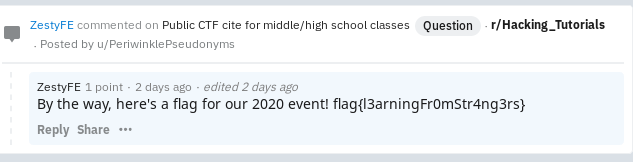
Since the creator of this challenge is ZestyFE I searched for his account in reddit.
The Big Stage
Hint : One time we keynoted @SaintCon… I think I remember hiding a flag in our pres
So I started googling about the conference and found a YT link
Did some fastforwarding at 1:49:40 found an example of a CTF flag.
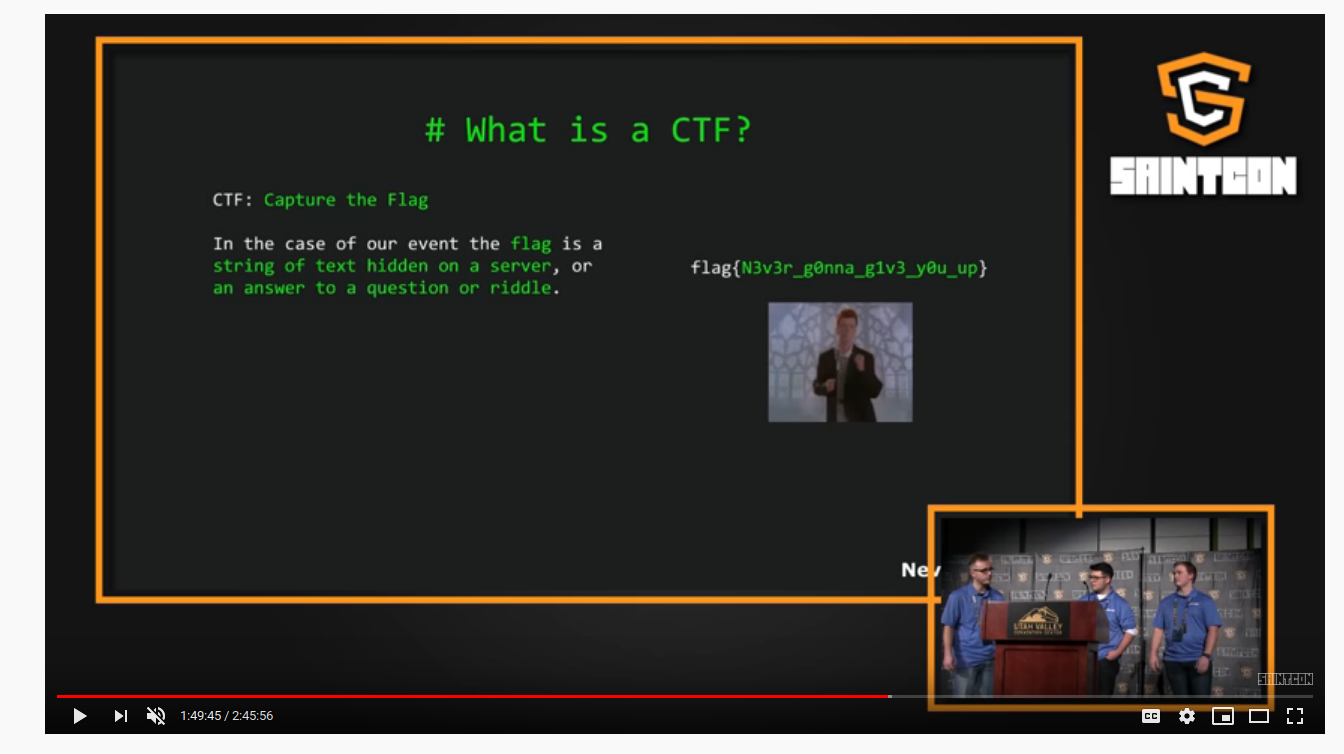
The Link
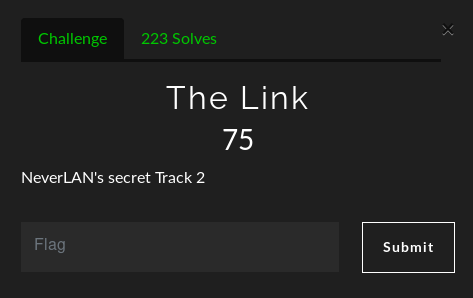
Hint : NeverLAN’s secret Track 2
Track represents Music maybe , when I register for CTF I saw Music category in the main page.
So I opened that and found Track1 Track2 Track3 (If its not displayed reload the page.)
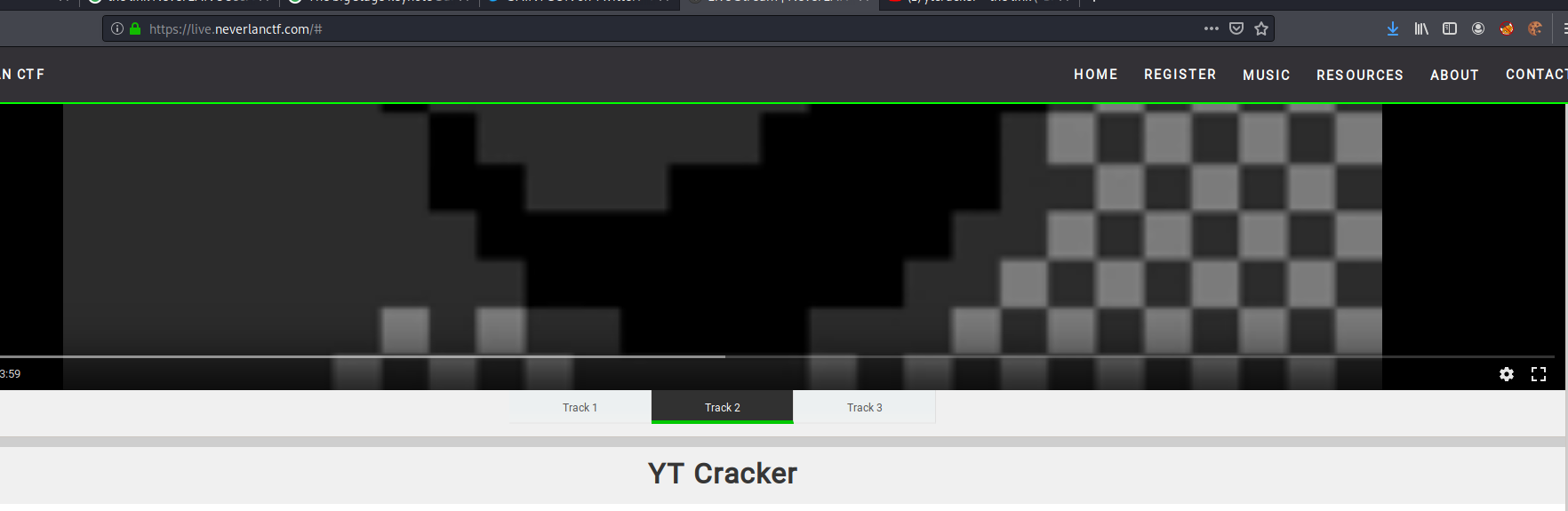
We know Track2 is what we want, Its an youtube video so I opened link directly to YT and found the flag in comments.
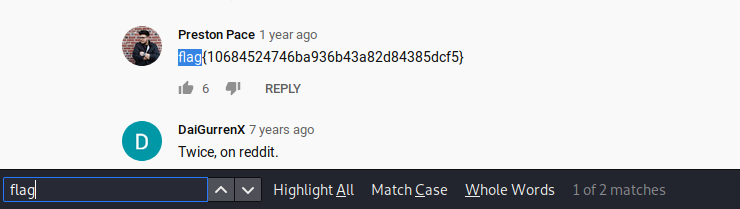
Thats just Phreaky
Hint : The first of many stories that have been told. 01 September 2017 | 14:01
From the given hints I googled and opened the first link which relates everything with the hint
Looks like some story.
I searched the flag in source code of the page.
Forensic
OpenBackPack
I started with strings and steghide not good results then I tried binwalk.
binwalk - tool for searching binary images for embedded files and executable code
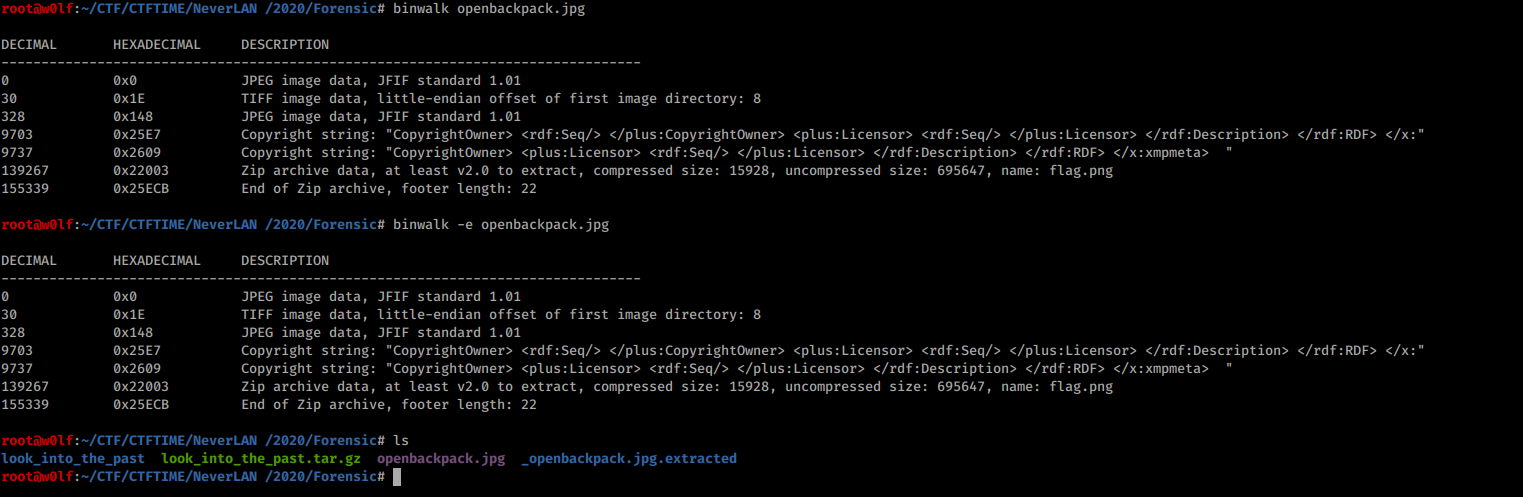 It extracted the files.
It extracted the files.
-e, --extract
Automatically extract known file types

Look into the past
I downloaded the file to my machine and extracted and started searching whats there.
root@w0lf:~/CTF/CTFTIME/NeverLAN /2020/Forensic/look_into_the_past/home/User# ls -la
total 52
drwxr-xr-x 9 1000 rvm 4096 Feb 8 21:54 .
drwxr-xr-x 3 1000 rvm 4096 Feb 8 21:54 ..
-rw-r--r-- 1 1000 rvm 349 Feb 7 00:03 .bash_history
-rw-r--r-- 1 1000 rvm 864 Feb 7 00:04 .bashrc
drwxr-xr-x 2 1000 rvm 4096 Feb 8 21:54 Desktop
drwxr-xr-x 2 1000 rvm 4096 Feb 8 22:22 Documents
drwxr-xr-x 2 1000 rvm 4096 Feb 8 21:54 Downloads
drwxr-xr-x 2 1000 rvm 4096 Feb 8 21:54 Music
drwxr-xr-x 2 1000 rvm 4096 Feb 8 21:54 Pictures
-rw-r--r-- 1 1000 rvm 672 Feb 7 00:04 .profile
drwxr-xr-x 2 1000 rvm 4096 Feb 8 21:54 Public
drwxr-xr-x 2 1000 rvm 4096 Feb 8 21:54 Videos
-rw-r--r-- 1 1000 rvm 37 Feb 7 00:03 .vimrc
Found .bash_history
In computing, various shells maintain a record of the commands issued by the user during the current session. The history command works with the command history list.
Found some commands history.
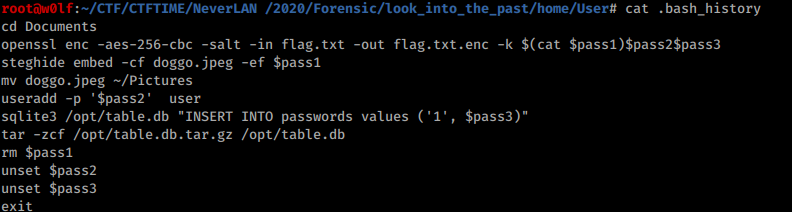
I looks like 3 passwords we created and decoded the flag.txt file to flag.txt.enc and the 3 passwords are split into 3 places
So I started from pass1
steghide embed -cf doggo.jpeg -ef $pass1
mv doggo.jpeg ~/Pictures
Its embeded in an image and its located in /Pictures
root@w0lf:~/CTF/CTFTIME/NeverLAN /2020/Forensic/look_into_the_past/home/User/Pictures# steghide extract -sf doggo.jpeg
Enter passphrase:
wrote extracted data to "steganopayload213658.txt".
root@w0lf:~/CTF/CTFTIME/NeverLAN /2020/Forensic/look_into_the_past/home/User/Pictures# ls
doggo.jpeg steganopayload213658.txt
root@w0lf:~/CTF/CTFTIME/NeverLAN /2020/Forensic/look_into_the_past/home/User/Pictures# cat steganopayload213658.txt
JXrTLzijLb
They didnt used any password so I left the passphrase empty.
pass2
useradd -p '$pass2' user
New user added with the name of user and pass2, basically passwords will be in /etc/shadows
I did cat /etc/shadows
user:KI6VWx09JJ:18011:0:99999:7:::
pass3
sqlite3 /opt/table.db "INSERT INTO passwords values ('1', $pass3)"
tar -zcf /opt/table.db.tar.gz /opt/table.db
A Sqlite Database created and pass3 inserted into passwords and its in /opt directory.
root@w0lf:~/CTF/CTFTIME/NeverLAN /2020/Forensic/look_into_the_past/opt# ls
table.db.tar
root@w0lf:~/CTF/CTFTIME/NeverLAN /2020/Forensic/look_into_the_past/opt# file table.db.tar
table.db.tar: POSIX tar archive
root@w0lf:~/CTF/CTFTIME/NeverLAN /2020/Forensic/look_into_the_past/opt# tar -xvf table.db.tar
table.db
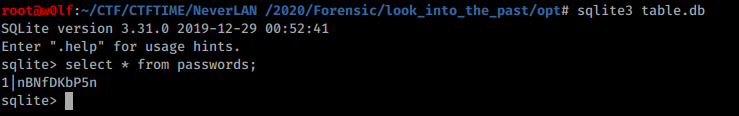
Got 3 pass now
We know they encrypted with openssl with these command
openssl enc -aes-256-cbc -salt -in flag.txt -out flag.txt.enc -k $(cat $pass1)$pass2$pass3
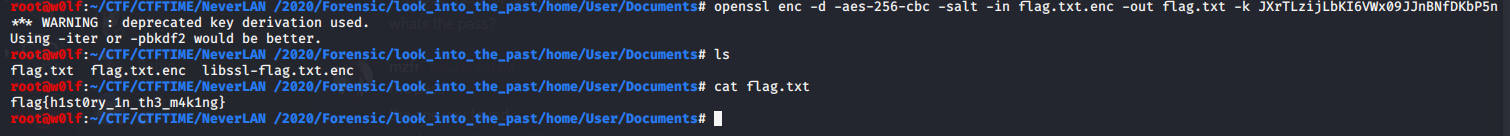
Now we can decrypt the flag.txt.enc to flag.txt with the passwords we found.
I combined all 3 passwords
openssl enc -d -aes-256-cbc -salt -in flag.txt.enc -out flag.txt -k JXrTLzijLbKI6VWx09JJnBNfDKbP5n
-d for decode
Chicken Little
Chicken Little 1
I logged in with the given credentials
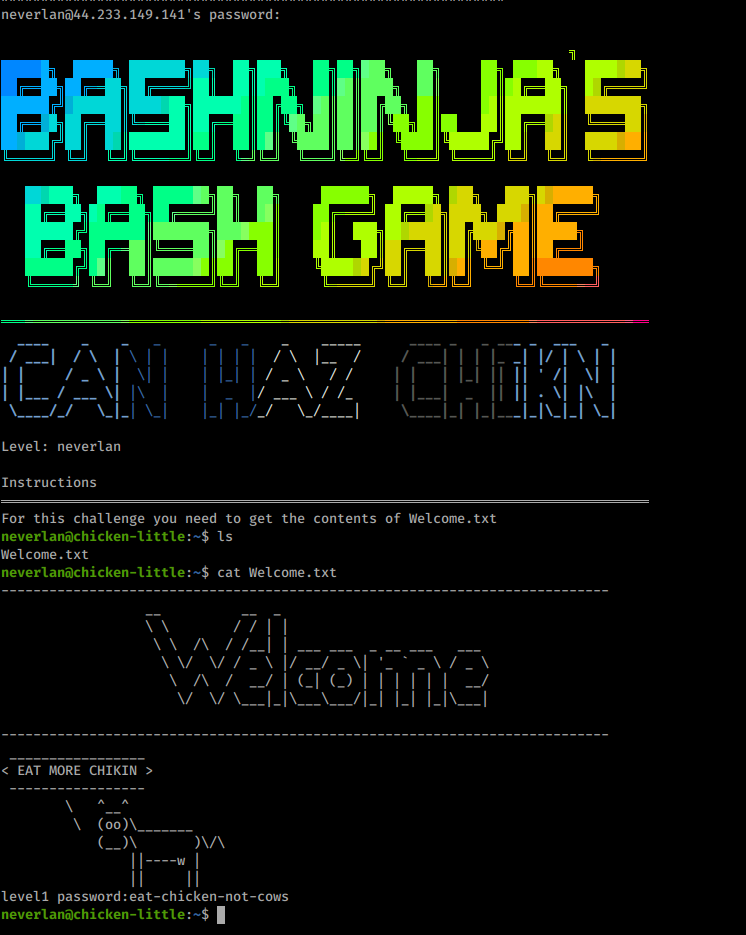
They Provide the password in Welcome.txt
Chicken Little 2
Hint : Password is hidden
We can view all files even hidden files using ls -la
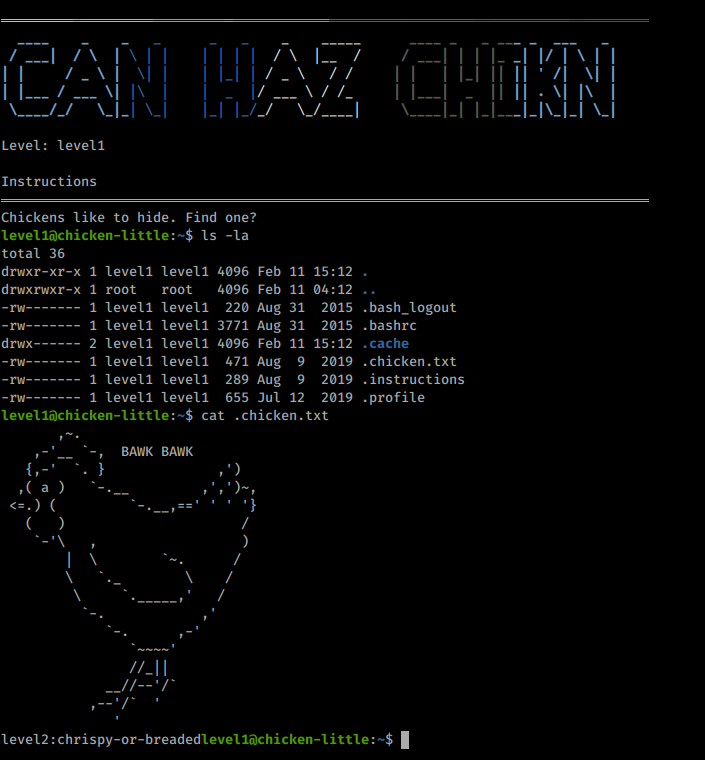
Chicken Little 3
If I cat the BAWKBAWK.txt it keeps on printing BAWK and We know that on every password has level before the password.
So I used grep that level
Chicken Little 4
Its a binary file so we can use strings to see printable characters in the file.
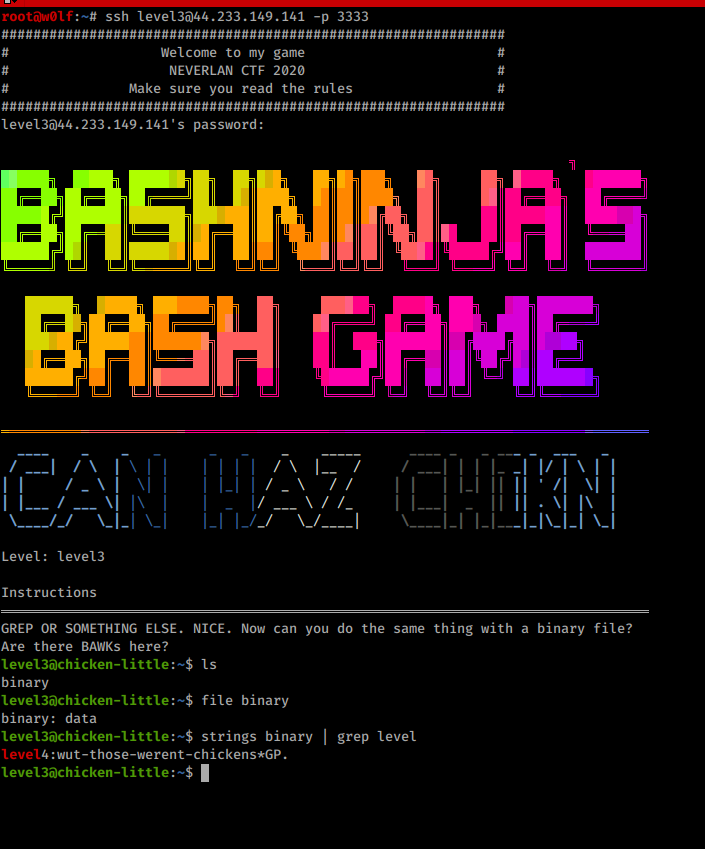
Chicken Little 5
This is an gzip file but I cant decompress it because the extension is missing, I added them and tried extracting.
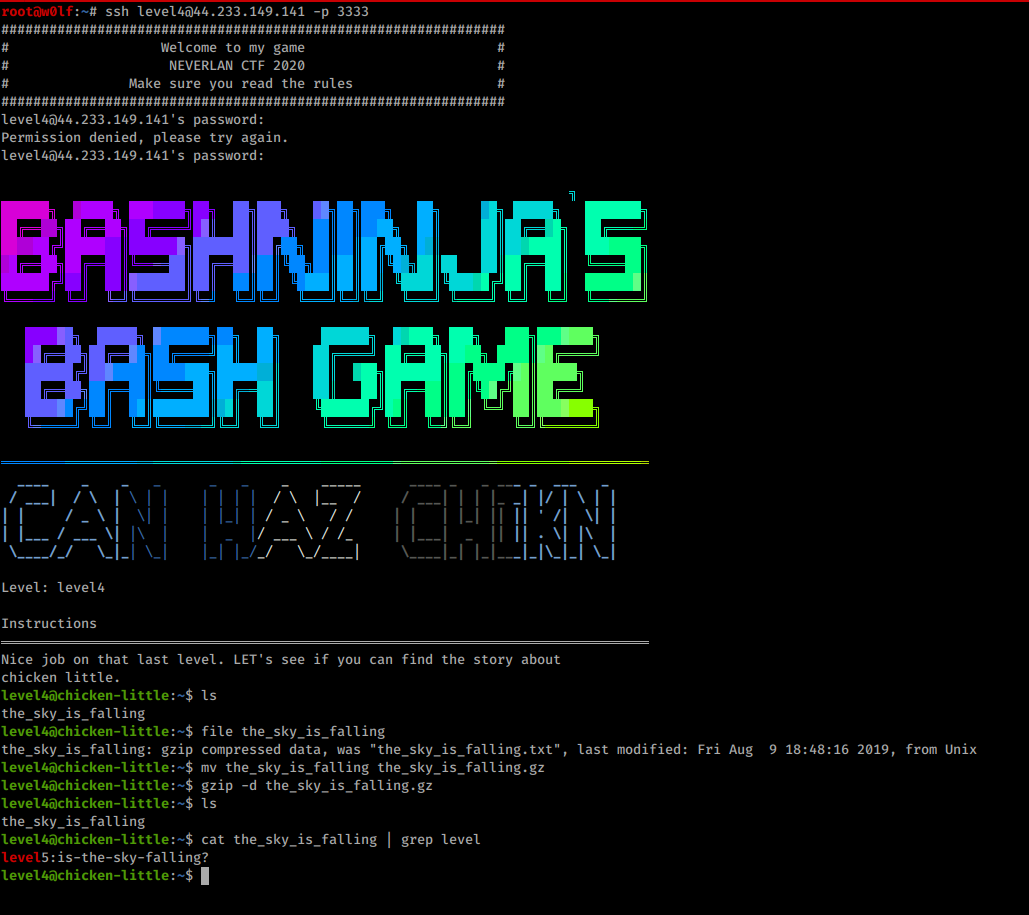
gzip -d the_sky_is_falling.gz
-d = decompress
Chicken Little 6
The Hint is we need to download the image file to our machine and see it

Reference : https://linuxize.com/post/how-to-use-scp-command-to-securely-transfer-files/
SCP (secure copy) is a command-line utility that allows you to securely copy files and directories between two locations. With scp , you can copy a file or directory: From your local system to a remote system

Chicken Little 7
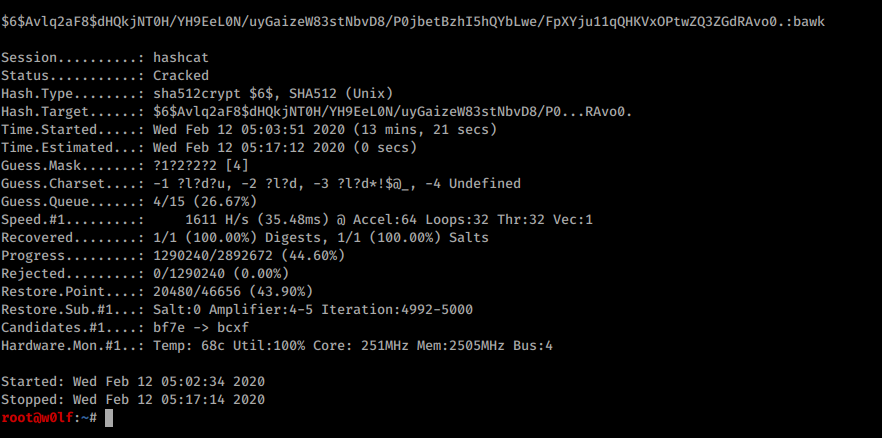
The Hint is we can get level7 password in normal hash location which is /etc/shadow and crack them using hashcat.
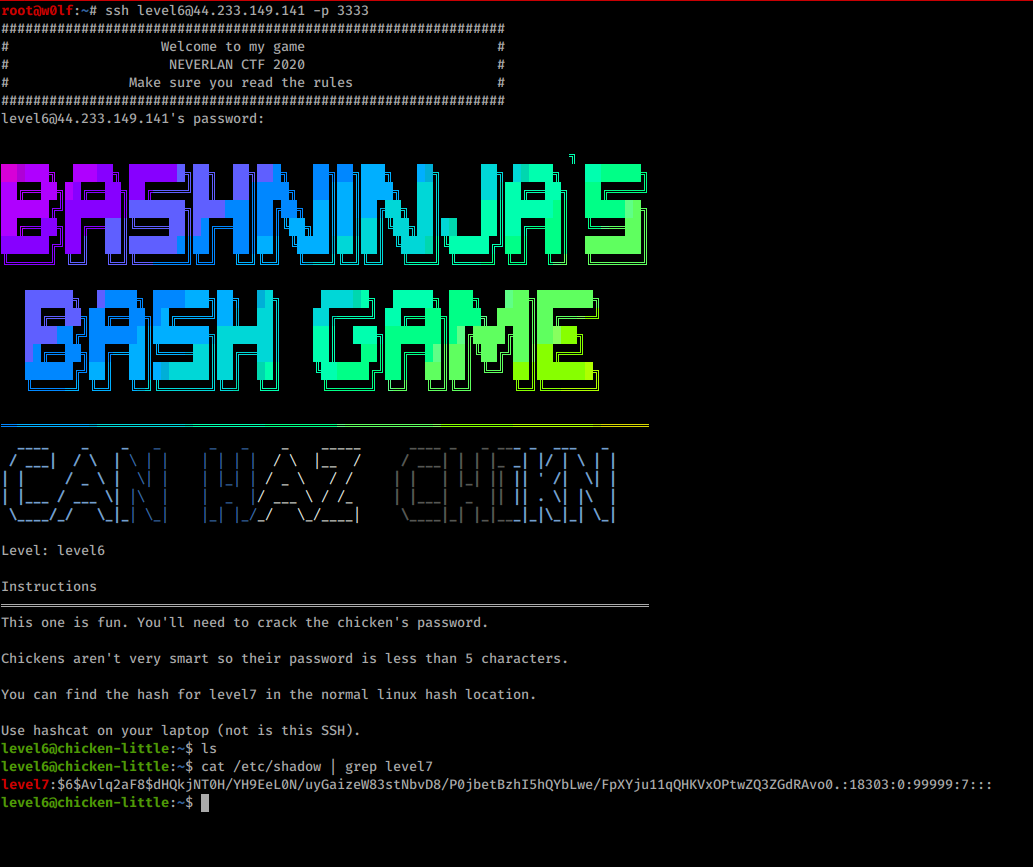
I copied the hashes to my machines and named it as hash
-m 1800 = sha512crypt
-a 3 = attack mode
How do you find its sha512crypt? I used john before that and it shows me what hash it is?
Trivia
Milk Please
Cookies were designed to be a reliable mechanism for websites to remember stateful information.
Flag:Cookies
Professional guessing
Flag:Password Cracking
Base 2^6
Flag:Base64
AAAAAAAAAAAAAA! I hate CVEs
With the give hint I googled the exploit
This is because of pwfeedback
Flag:pwfeedback
Rick Rolled by the NSA???
I googled with the hint
Flag: CVE-2020-0601
We managed to get into the position of 136 out of 1121